Travel Suppliers = Easy Pickings For Hackers
Doug Clare, vice
president of product management for Fico, an analytics software company, said
the travel industry gets hit “pretty hard” with fraudulent transactions. The top
reasons:
Anonymity
Booking a ticket or
hotel room online is anonymous.
Acceptance Of Arrangers
Common practices
allow cardholders to book trips for others.
Card Matching Not Required
Airport counters and
kiosks don’t ask for the card with which the flight was purchased; the same
goes for hotel reservations.
The avalanche began
with Starwood.
On Nov. 20, 2015,
Starwood Hotels & Resorts Worldwide announced that malware had infected
point-of-sale systems at 54 of its North American hotels, including 26 Westins,
18 Sheratons and seven W-branded hotels. The malware targeted cardholder names,
card numbers, security codes and expiration dates.
Then, five days
later, Hilton released a statement that it, too, had been the victim of malware
attacks on POS systems at an undisclosed number of its properties and that
payment card information had been accessed.
Two days before
Christmas, it was Hyatt's turn to disclose that cybercriminals going after
payment card information had targeted its hotels. In that breach, POS systems
at restaurants, spas, golf shops, parking facilities and a "limited number"
of front desks were affected.
Within the span of
34 days, three of the most recognized companies in the hotel industry announced
major breaches of customer payment data. But they weren't the first to make
such an announcement in 2015. In July, the Trump Hotel Collection announced it
appeared to have been the victim of malware attacks on POS systems, later
confirming seven properties were affected. In April, previous hacking victim
White Lodging Hotel Services Corp. announced POS systems at 10 of its
franchised hotels had again been compromised. The month prior, Mandarin
Oriental Hotel Group disclosed hacks at "an isolated number" of
hotels in the United States and Europe.
Why Hotels?
Cybercrime threats
to the lodging industry are nothing new, but the volume of attacks going after
guest card payment information raises the question, why does this keep
happening to hotels? But that question is, perhaps, a flawed one. Chris Zoladz,
founder of Navigate LLC, an information protection and privacy consultancy,
suggests POS systems are the larger target, and those exist well beyond the
hospitality industry.
According to Privacy
Rights Clearinghouse, a nonprofit group that keeps a chronology of all manner
of data breaches disclosed to the public through company releases and media
reports, there were 111 breaches related to hacking or malware on POS systems
during 2015. Of that total, only seven of the breached entities were hotel
companies. Others on that 2015 list included Sabre, United Airlines, American
Airlines, Uber, Starbucks and Chick-fil-A.
Chip Cards Help, Right?
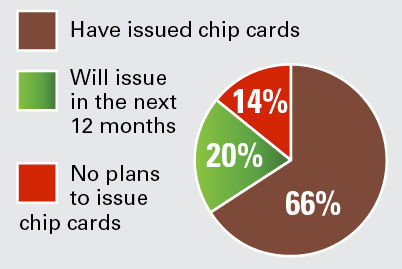 Business Travel News survey of 198 travel buyers
Business Travel News survey of 198 travel buyers
They add security within the point-of-sale environment, but card-not-present transactions and holding card numbers on file remain risky.
"POS systems
are often the weak link in the chain and the choice of malware," said Mark
Bower, HPE Security global director of product management for enterprise data security.
"They should be isolated from other networks but often are connected. A
check-out terminal in constant use is usually less frequently patched and
updated and is thus vulnerable to all manner of malware compromising the system
to gain access to cardholder data."
Instead of why
hotels, a better question is what is it about hotels. What makes their
POS systems particularly vulnerable and valuable to hackers?
Bower suggests the
type of POS systems used at hotels are part of the problem. "These are
often integrated POS environments running applications in an environment that
is not as secure as modern hardened payment terminals designed to capture
payment data and implement encryption independent from the POS itself."
With integrated POS
systems, multiple POS feeds converge in the back-office system or electronic
cash register, whereas a semi-integrated or "hardened" system sends
encrypted data directly to the payment processor. The extra stop in integrated
systems creates a weakness that cybercriminals are quick to tap.
In addition, hotels
deal with a high volume of payment card transactions—between restaurants,
on-site shops, spas, parking facilities and front-desk billing—and card
information is stored with the hotel in the run-up to, and duration of, a
single stay.
"If you call a
hotel to make a reservation, they manually type in your card information and
leave your credit card on file," said Shaun Murphy, founder and CEO of
SNDR, a message- and file-sharing app, who specializes in cybersecurity. "Your
personal details are stored in so many different systems, there are so many
more ways for malware to have access to them."
What Travel Managers Care About
68%
Mitigating
unauthorized charges incurred on corporate cards
81%
Protecting
travelers’ personally identifiable information/identity theft
61%
Protecting
corporate travel information/location of travelers
Source: Business Travel News survey of 198 travel buyers
The hospitality
industry, too, suffers from a high turnover of employees and staff members. The
overall turnover rate in the restaurant-and-accommodations sector was 66.3
percent in 2014, according to the U.S. Bureau of Labor Statistics' most recent
figures. If a hotel is regularly losing staff members and hiring new ones, it
can be difficult to ensure each is well trained in handling guest data.
Individuals who work
in a hotel restaurant or behind the front desk are rarely IT people, meaning
staff members are often completely dependent on a POS system installer to make
sure everything is programmed correctly. Think of a POS system like a garden hose.
It doesn't matter how good the hose is, Zoladz said, if it's improperly
installed, there are going to be some leaks. Murphy said after such software is
installed, "a lot of times [hotels] don't have mobile IT systems to make sure
the systems are monitored."
Basically, if the
hose becomes defective, it may take a while for anyone to notice.
In the Hilton
breaches, hotels were hit between Nov. 18 and Dec. 5, 2014, then once more from
April 21 to July 27, 2015. According to security blog Krebs on Security, that
breach wasn't discovered until August, when Visa confidentially alerted
multiple financial institutions that cards used at a brick-and-mortar entity
were compromised.
"You have my
personal assurance that we take this matter very seriously, and we immediately
launched an investigation and further strengthened our systems," executive
vice president of global brands Jim Holthouser said in a statement during
Hilton's November disclosure.
A Hilton
spokesperson told Travel Procurement the company had no further
information to share about the number of hotels affected by the incident or the
type of malware found by forensic experts. Timelines for other breaches, from
when the attacks occurred to when an investigation was launched, are less clear
in the other hotel incidents disclosed in 2015.
"The malware
frameworks that the point-of-sale operators are ... infected with is very, very
sophisticated," Murphy said. "These hackers go out and they find a
top point-of-sale operation system and they figure out how to breach it."
Last year, global
cyber-threat intelligence company, iSight Partners made a concerted effort to
educate companies within the retail, healthcare, food services and hospitality
sectors about the newest and most sophisticated POS system malware, ModPOS.
Stephen Ward, senior director and spokesperson for iSight, said the company
doesn't believe ModPOS is the malware behind the recent hotel malware attacks.
But the module, which is customized to its targeted environment and is
extremely difficult to detect, demonstrates how such attack systems are
evolving.
What Is The Legal Responsibility Of Hotels?
The structure of the
hotel industry is complicated and fragmented. With big hoteliers making their
money mostly through franchise agreements with owners and separate companies
managing hotels on behalf of franchisees, it's not always clear which party is
responsible for what at any single branded property. The legal landscape around
customer payment and privacy can be similarly difficult to navigate.
"There are a
lot of places where regulation of data-security conduct can come from in the
hotel industry," said Sandy Garfinkel, chair of law firm Eckert Seamans'
data security and privacy practice group.
The first place,
Garfinkel said, is through the Payment Card Industry Data Security Standard, a
set of requirements "designed to ensure that all companies that process,
store or transmit credit card information maintain a secure environment,"
according to the PCI compliance guide. It's not law, Garfinkel said, but it
helps the credit card industry avoid liability.
Contracts also tell
hotel companies and franchisees how to handle cybersecurity. "More and
more you have hotels, especially franchised hotels, having their data-security
practices controlled or regulated through contracts with franchisors—or on a
lower level it may be a contract between a manager and an owner—that imposes
data-security standards of conduct and policies on whoever operates the hotel,"
Garfinkel said. "Those wouldn't be case law, statutes or regulations, but
they would be contractual, legally binding provisions that say you must handle
data in a certain way."
Garfinkel said the
growing practice of regulating data security through contracts is a direct
result of the best-known hotel data breach, at Wyndham Worldwide, in which
hackers infiltrated the corporate computer system and the systems of individual
properties between 2008 and early 2010, stealing payment card information from
hundreds of thousands of guests. The U.S. Federal Trade Commission sued Wyndham
in 2012, alleging Wyndham failed to take proper cybersecurity measures to
protect customer information. The FTC settled the suit with Wyndham in early
December 2015, and the hotel company must comply with several orders, including
establishing a data-security program to protect cardholder data processed in
the United States.
"Wyndham has
woken up the hotel industry to be more aware and proactive about data breaches
and data security," Garfinkel said. "Not that it's where it should
be, but there's been much more attention." Though the contracts can seem
like nothing more than legal finger-pointing, he said the heightened fears of
liability and damage to a company's reputation have brought the industry along.
After a breach
occurs, things can get even more complicated. The United States doesn't have a
comprehensive federal data-security law. Instead, that power is handed over to
the states. "Right now, there are 47 different states with 47 different
data-breach response laws, which have a lot of consistencies but some of which
are wildly inconsistent," Garfinkel said.
These state laws
vary in how customers should be notified of a breach, how soon they need to be
notified and whether a hotel should have a written information security plan prior
to any breach. Complicating matters further, when a breach does occur, a hotel
is not beholden to the laws of the state in which it's headquartered or even to
the laws of the state in which breaches occurred. Instead, hotels must follow
the notification laws of the state in which each individual guest resides. "If
a hotel has a data breach and people from 25 different states have stayed at
the hotel during the time of the breach and are affected by the breach,"
Garfinkel said, "the hotel, by statute, must comply with all 25 of those
state's laws when it comes to responding to the breach."
What Can Travel Managers Do?
The onslaught of
threats from cybercriminals can cause fatigue in travel managers.
"I always have
concerns about me personally and any of our travelers; they all have individual
cards," said Christel Peterson, corporate services and travel manager
associate at Exp. "But I don't think in this tech world there's any way
around it."
To protect their
travelers and to ensure hotels take the proper steps in protecting their
security, travel managers can start by putting special provisions in their
hotel contracts.
Garfinkel, who
reviews sales contracts for his hotel clients for both meetings and transient
business, said in the past two years he's seen an uptick in the number of
companies putting special data-security riders into their contracts.
"They say, 'As
part of all this and the money we're going to pay you for having our [business]
at the hotel, you also agree that your hotel is compliant with PCI, that your
hotel's data-security measures obey or comply with applicable law and that you
will use the utmost care in handling our individual employees' personal
identifying information," he explained. "You could even have indemnification
provisions if the information is stolen while in the hotel's possession."
Ensuring Data Security: A Sourcing Guide
PCI Compliance
See if the supplier complies with these 12 requirements, defined by the
payments card industry to ensure a merchant systems security baseline.
Local Compliance
Confirm that data-security measures comply with local laws.
Semi- Versus
Fully-
Integrated POS
Fully-integrated systems have more connection points for malware and
less encryption. Ask your supplier.
Plan Of Action
Vet the supplier’s plan of action for data breaches.
Indemnification
If possible, include an indemnification clause in the hotel contract
and define penalties for failure to protect data.
In 2014, Interpublic
Group vice president of global travel and corporate card services Fran
McClarnon told Business Travel News she had begun requiring a $10
million indemnification from suppliers that handle her company's data
consolidation and reporting.
This year, the
company specifically assigned a resource to ensure all airline contracts worth
over $5 million of spend include clauses that address data security and
privacy, regardless of whether the contracts are up for renewal or not.
Airlines with renewal contracts have so far adhered to her requests. "We
give them enough business. If they're worried about losing it, they usually try
to compromise and come to the table with a solution and typically we get what
we need," she said.
Interpublic has
stopped short of requiring the same from hotels, in large part due to the fact
that transient travel contracts are negotiated through a tool, not a legal,
signed document. This makes it nearly impossible to insert an addendum,
according to McClarnon. But she believes suppliers are taking data security
more seriously as a result of corporations like hers taking it more seriously.
Garfinkel would
encourage travel buyers to keep pressing for change both on transient and group
contracts. "It really depends on your negotiating power,"
individually, yes, but also as an industry.
—Additional
reporting by JoAnn Deluna